Botnets are networks of compromised computers, controlled by remote attackers in order to perform such illicit tasks as sending spam or attacking other computers. The word Bot comes from the word Robot and is referred to any software program that carries out automated pre-defined tasks. They can perform useful tasks as well as malicious tasks. Webmasters may be familiar with the Google bot or the Bing bot that looks for and crawls fresh content on the Internet.
What is a Botnet

Bots can also be used to act like malware and carry out malicious tasks. Then can be used to assemble a network of computers and then compromise them. These are called Computer Botnets and can be controlled remotely by hackers or Bot Herders.
Each computer in the Botnet is called a Node and they could be any computer, anywhere in the world – even yours, if an attacker has managed to surreptitiously install malware on your computer, by exploiting vulnerabilities in your operating system or installed software, or by tricking you into installing it. Such Nodes are then used to spread the malware further, send spam mail or even attack other computers. Such Botnets are controlled en masse via protocols such as IRC. Some of you may want to learn more about Botnets.
Microsoft Malware Protection Center defines botnet as a network of computers that can be illicitly and secretly controlled at will by an attacker and commanded to take a variety of actions. Under this definition, a trojan downloader that is only designed to download arbitrary files and cannot otherwise be controlled by the attacker would not be considered a bot.
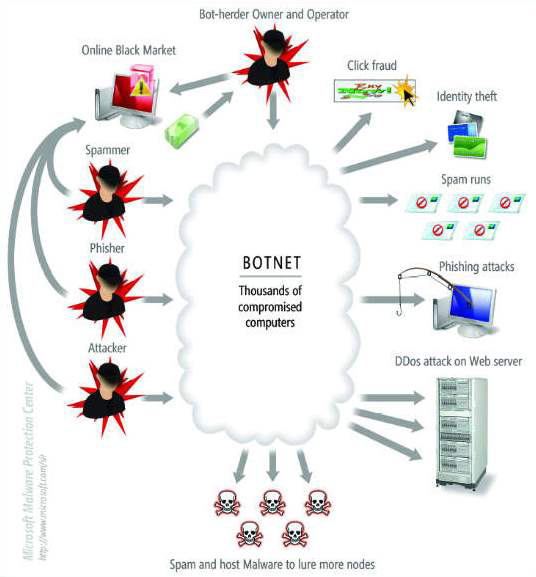
Botnets should be of concern to governments and businesses because of their ability to harness large numbers of individual computers to direct an attack against information technology infrastructure.
Microsoft is taking an aggressive approach to fighting botnets by collaborating with governments and others to take them down. Microsoft is also providing businesses, governments, and consumers with security tools and guidance. Working towards this goal, Microsoft has released a document titled Botnets: Guidance for Governments, which can be downloaded at Microsoft.
Infographic
McAfee has created a nice easy-to-understand Infographic explaining, what are botnets. With the rapid growth in malware and bot infections all around, it becomes important for all to understand what Botnets are and what Zombies are.
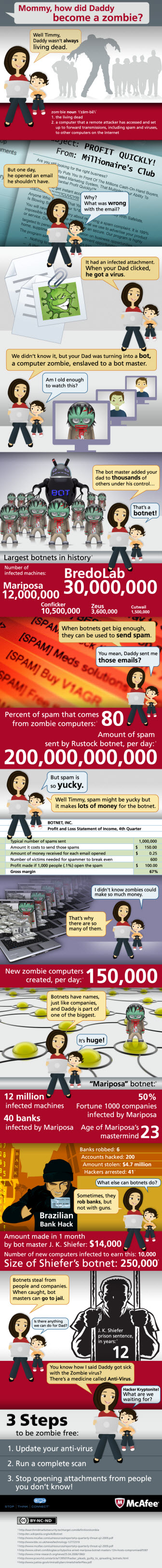
This Infographic nails the botnet lifecycle and economics just right… not too technical, not too simple. Click on it to see the larger image.
Fear that your computer may be a part of a Botnet? Have a look at these Botnet Removal Tools. This Global Botnet Visualizer keeps you up-to-date on Bot activity. These Botnet Trackers will help you keep track of the Bot activity globally.
Is a botnet attack illegal?
If you or anyone operators a botnet attack, it’s illegal, and mostly punishable by law. While every Botnet attack has a different purpose, a lot of data is stolen, and a lot of time and work is hampered. Imagine a hospital not able to register for incoming patients because the system has been taken down by a botnet attack.
Can a VPN protect you from DDoS?
No, it cannot, but it can hide your primary PC helping you safeguard the data on the PC. However, the VPN has to include security measures to ensure your data is not compromised.